PSD Concepts: How to Detect Surveillance and Counter
PSD Concepts: How to Detect Surveillance and Counter
- PSD Concepts: Introduction and Daily Routes
- PSD Concepts: How to Detect Surveillance and Counter
- PSD Concepts: Attack Recognition and the Art of the Ambush
- PSD Concepts: Why You Should Conduct Vehicle Searches
There are many types of surveillance detection and today we’ll be continuing to apply concepts and tactics used by Personal Security Detail (PSD) teams, with ways to detect static and mobile surveillance along your routes.
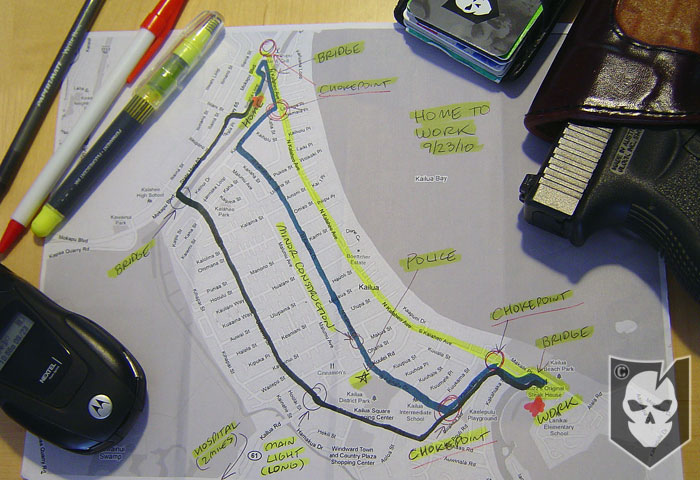
In our last article about Route Surveys we focused on going from home to work and we’ll be doing the same in this article.
I’m sure everyone wants to dive right into how you can ditch a “tail” and other counter surveillance techniques, but before you can do that you have to have a understanding how the surveillance process works.
What is Surveillance?
One definition I like is “The secret, continuous, periodic watching of persons, vehicles, places or objects to obtain information concerning the activities and identities of individuals.” It’s all about information gathering.
As I stated in the first article, you probably won’t to have to worry about a well organized group of terrorists following you from home to work, but even common burglars use basic surveillance methods to figure out when the best time to break into a residence is.
When we talk about terrorists or other organized criminals, they use a planning process that assures their success. If you are attacked they have already assessed your physical security and routines. Surveillance detection is using countermeasures to deny them information during the selecting and collecting phases. You also want to appear as a hard target, so they move on to someone else.
There is a common sequence of events that takes place during surveillance:
- Attackers select a potential victim and begin collecting information.
- Surveillance continues as the attack is planned and practiced.
- Attackers deploy according to the information received.
Surveillance is also used to confirm your arrival immediately prior to an attack. Once the attack has begun the attackers have a huge advantage. They have set the time and place that you are the most vulnerable and most exposed. The key to beating them is to identify and exploit their information gathering process (the surveillance itself) and hopefully end the attack before it begins. Make them move on to the easy target or make them realize they are going to have a fight on their hands. I know I keep saying “make them move on to someone else”, but that is exactly what you want to have happen.
Surveillance may take weeks, months, or even years. During the collection phase attackers are vulnerable to detection. This is also where you can use misinformation to confuse and delay their information gathering.
The duration of the surveillance is a major factor and shows why it’s difficult to detect the common burglar or crime of opportunity. Their surveillance is normally just hours and they may not be open to detection over that short period of time. This is where being a hard target comes into play.
Detection Techniques
Your driveway
- Be dialed in and keep your head on a swivel. Even the appearance that you are looking around can be helpful. Looking around may make the person watching you think you are looking right at them. This is referred to as being “hot,” when conducting surveillance there is nothing worse than feeling like the target is on to you or your vehicle.
- This may make them have to “cool off” and switch out the “eyeball” (the person watching you). They are susceptible to detection when they switch personnel out. One vehicle may leave a position and be replaced by another in a different location. If both of these have a good vantage point to your front door or street that may indicate you are being watched.
- One of the upcoming articles will be about checking your vehicle. I won’t get into that yet, but one story I’ve heard comes to mind. An officer was stationed overseas and each morning before leaving for work he would lift the hood of his car and look around and under the engine. He had no idea he was being watched during the selection phase of a surveillance. The terrorists thought he was dialed in and was checking for bombs each morning. What they didn’t know was he had an oil leak and he was just trying to figure out where it was coming from. He was passed over and they moved on to someone else.
- This shows how the small things you do can confuse and mislead the information collection process.
The take-away
- By far the toughest part of a surveillance is what’s called the take-away. This is when the target (you in this case) leaves a location and starts moving. If the eyeball isn’t paying attention and the other members aren’t ready, you can lose them right from the start. I speak from personal experience on this one as I’ve dropped the ball on a take-away or two. As I mentioned in the route survey article, you cannot be alert 100% of the time. This also goes for someone who is attempting to watch you.
- You have some factors working for you as well. Your direction is not usually known (since you switch things up), evasive moves can be made early, they are not sure when you may move and you may move quickly. You want to disrupt the take-away.
- Every once in awhile you can leave as normal and circle around the block right back to your house. Look around for vehicles or people moving. I do this all the time as I’m on a corner lot and I can take the alley way to make a loop.
- Since you are using different routes, once you clear your first choke point you will make it difficult for them to find and follow you again.
- Keep in mind you can still be picked up when you arrive at work or the last choke point on your route. But the key here is not to let them gather information on the routes you take. There may be a great attack site on one of your routes, but if you deny them the opportunity to follow you on that route they may not know about it.
En route
- Since you have conducted your route reconnaissance you know where your choke points and ideal attack sites are. These are the areas where you need to be vigilant. These are also the areas where you can attempt to detect if someone is following you, which is called “checking yourself”.
- There are numerous ways to check yourself and it’s only limited by your time and creativity. You do have to use common sense though, driving into that ten story parking garage, parking your car, going up and down two separate elevators and then driving out the same entrance you just drove in is not going to work.
- Speeding up, slowing down, making three right turns, stalling at a green light, taking a one way street, and making a dead stop are a few techniques you can use. You have to pay attention to what is going on around you and how people/vehicles are reacting to what you are doing. If not you are just wasting your time.
- The TAC team I’m assigned to once followed a guy who was making all those moves. It wasn’t that difficult to keep an eye on him because he was doing those things without even glancing out of his rear view mirror. He wasn’t effective at all since he was just being a putz and not watching how we were reacting and adjusting. We were able to follow him and all those moves were made in vain.
- SPEED: Just because you drive like Ken Block through traffic doesn’t mean you can’t be followed. I would say unless you know for an absolute fact you are being followed, drive your normal speed. Employ your counter-moves to try to detect the surveillance, but unless you’re coming under attack, crashing your car or getting a citation isn’t worth it. It’s going to be impossible to tell an Officer you thought you were being followed so you were going 30 over (unless you actually were and called 911 to report it).
- Since we are talking about individual techniques you won’t have the luxury of having “agents” set up a Surveillance Detection Route. An SDR is used to detect surveillance along your route but you have to have someone as your eyeball for it to be truly effective. I’m pretty sure your significant other won’t be thrilled with the thought of sitting on a street corner everyday for a month to see if the same car keeps following you to work.
- A simple SDR you can set up for yourself would be in a residential area you are familiar with. Find a route that snakes you deep into the neighborhood and ends in a cul-de-sac. The best end location would be a cul-de-sac that has a sharp or continuous turn going into it, the kind that surprise you when you drive into it.
- Once you enter the cul-de-sac get in a position to exit quickly if someone follows you in. If they do make sure to write down the description of the vehicle and people.
- This type of SDR is only going to work if you are the only one that knows the area or if the person following you doesn’t have GPS. If they figure it out they will just set up and wait for you to leave. Also if you are unknowingly in the attack phase you may have just backed yourself into a corner. This shows that you really need another eyeball to use an SDR correctly.
- Look at the people along your route. Do they have a valid reason to be there? Is that guy at the bus stop watching you or simply waiting for the bus? Do they fit in to the environment, meaning does that guy in the construction hat look like he knows what he is doing? It takes a lot of practice doing surveillance to be able to use a ruse or disguise effectively. If you’re sharp you should be able to pick out that odd person that just doesn’t fit.
- Does a vehicle move when you move? Does a parked vehicle leave the area in the opposite direction each time you pass? Multiple sightings of the same person, vehicle, or activity may confirm you’re being watched.
The arrival
- Just like leaving your residence, your arrival requires your attention. So does the last choke point along your route.
- Since you may have ditched your tail at the take-away, someone may have leapfrogged to your destination. That is one of the golden rules of surveillance; if you lose your target go to where you know they will show up. In this case it’s your work address.
- Switch up your parking spots and take different entrances into the parking area. Can you find a spot that would make it difficult for the eyeball to see your vehicle? This can help with your take-away.
- If you’re dealing with a one person surveillance he/she is most likely going to be in the same vehicle. If the same car shows up at home and work, that’s called a clue.
- If you are dealing with trained subjects you have to show them you are switched on when you arrive at work just like you are at home.
So what does all of this accomplish? If you can deny information gathering and show yourself as a hard target you will force the attackers to make a couple of choices.
- They will move on to someone else (sounds familiar I know).
- They will be forced to choose attack sites that are in your favor and give you the tactical advantage.
- Even if they pick out the first and last choke point in your route, you will be ready and have a plan in place if a attack happens. Of course, the best plan goes out the window when the bullets start to fly, but you will greatly enhance your (and your families) chances of coming out alive.
Wrap-up
The take home message from this article is that if you suspect surveillance you should alter your route and times to avoid a possible attack. This will cause unpredictability and confuse the attackers. You should also take notes of suspicious activity, vehicles and persons. This will let you put the pieces of the puzzle together and confirm your suspicions.
If warranted contact the police and report the suspicious activities. You may just catch that burglar during his surveillance after all!
I would highly recommend taking a class on how to conduct surveillance from a reputable source such as SCG International. This will help you immensely and only through truly understanding how surveillance works can you learn how to counter it.
When Bryan and I discussed writing this series of articles I had to think carefully about what information I was going to put out, as I want this information to be used to keep you and your family safe and have it become an important part of your overall security plan. That is the intent of these articles and discussing ways to keep you safe is the foundation of ITS Tactical.
That being said, there are plenty of places on the Internet where you can find information on how to conduct surveillance and surveillance detection. “Bad guys” have a lot of resources and I don’t feel writing these articles will help them any more than they can already help themselves.
Stay tuned for our next article on attack recognition and post up any questions in the comments below.










Discussion