Spectre & Meltdown: Newly Discovered Vulnerabilities that Affect Almost All Computing Devices
Spectre & Meltdown: Newly Discovered Vulnerabilities that Affect Almost All Computing Devices
Early this year, two variations of a major electronic security vulnerability were discovered. These vulnerabilities have existed for 20 years, but no one has come forward with the information until now. This means that they may have been used before, just not publicly shared.
To sum it up, Spectre and Meltdown are the names used to describe variations of a vulnerability that affects almost all computer chips manufactured in last 20 years. That means everything from your Hewlett Packard laptop to your Apple iPhone is affected by these vulnerabilities.
What are the Vulnerabilities?
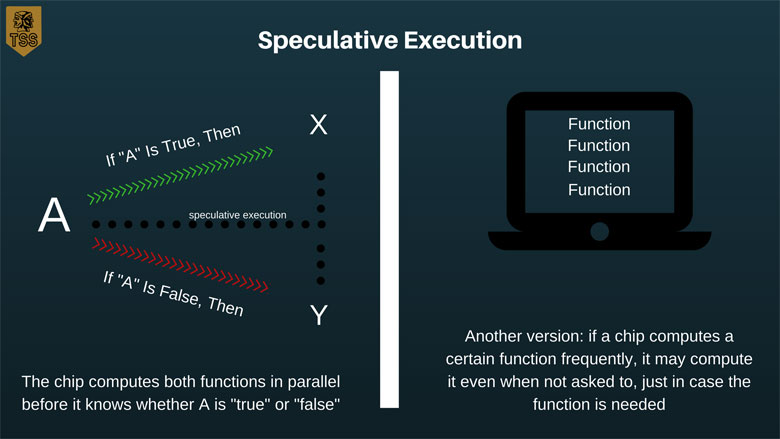
By using these vulnerabilities, a malicious program can gain access to and spy on data that it shouldn’t be allowed to see. The attack exploits two features in computer chips used to increase speed, one called speculative execution and the other called caching.
Speculative execution is a fancy term for when a computer chip works ahead to improve speed. The chip will find the solutions to both outcomes of the current choice before the choice is made
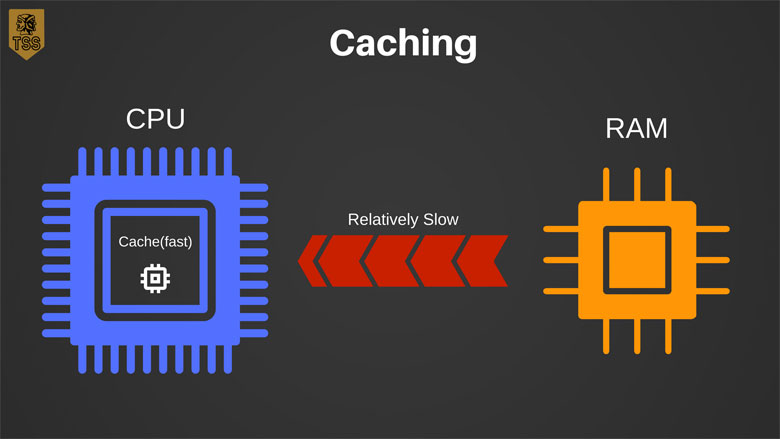
Caching is a process used to speed up memory access. It takes a long time for a computer’s CPU to get data from RAM (Random Access Memory) because it’s located on a separate chip. To get around this, there’s a small amount of memory on the CPU chip. This allows fast retrieval of data that the chip will soon need. Often times the output of speculative execution is stored in the CPU cache.
This is where it gets messy. Speculative execution and caching are part of protected memory, which houses the vulnerability that Spectre and Meltdown attacks take advantage of.
What is Protected Memory?
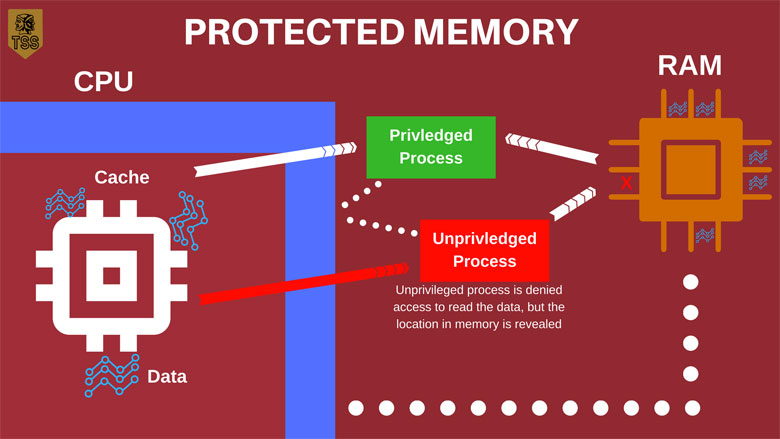
Protected memory is fundamental to computer security, as without it, any process would be able to access any data; whether it should be able to or not. With protected memory, programs are able to keep their data private from users and other programs.
If a process wants to access data, it must undergo a privilege check. Here lies the key to understanding the vulnerability. A privilege check can take a long time and while the CPU is waiting, it starts working with the data through speculative execution, even though the CPU hasn’t received permission yet. Now you might be thinking “What’s the big deal?” because the speculative execution results are still protected at the hardware level through the privilege check.
However, because the data is stored in the CPU cache before privilege is granted and because the CPU cache can be accessed quickly, a process can try to access certain memory locations in an attempt to see if that data’s been cached. Even though the process can’t read the memory because it doesn’t have the privilege to do so, it can figure out what the data is by identifying that memory location. This is also known as a side channel attack.
While this is definitely a complicated subject, a complete understanding of the vulnerabilities isn’t necessary to protect against them. What you really need to know is what can happen and how to prevent it.
Prevention

At this point you might be wondering what this all means to you. Do hackers know your passwords? Have your credit cards been compromised if you’ve shopped online? Is the world going to end? Not quite, but there are still some things you should be concerned about, as Spectre and Meltdown open the door for many dangerous attacks.
For instance, malicious code on a website could trick your browser into divulging user and password data. These attacks could also cause the leak of information through many cloud computing services.
The worst part of this discovery means that all secure code (code that was written to be secure with the assumption that the underlying hardware was secure) is no longer secure. So now that we know that, let’s examine some steps you can take to minimize the risks of these vulnerabilities.
If you use shared-hosting (i.e. cloud) services, you should check with your service provider to confirm they’ve applied security updates to address these vulnerabilities. Locally, you should deploy security updates to all systems and devices as soon as they become available. Additionally, consider discontinuing the use of systems that cannot be updated.
Ensure you’re using good anti-virus/anti-malware software on your computers and frequently update your operating systems to the latest version. When deleting files, ensure that you’re employing methods of digital shredding, whether using software or system tools built into your operating system. Lastly, make sure your firewall is enabled to prevent unwanted intrusion.
When you’re in public, don’t leave any of your devices unattended. For devices that include administrator accounts, consider disabling these unless absolutely necessary. In public and in private, beware of phishing attacks or social engineering methods. In a phishing attempt, an attacker will create a false login page to get a user to input their credentials. Social engineering attempts usually involve an attacker pretending to be an official organization or authority figure, in an effort to get a user to divulge sensitive information. An example of a social engineering attack would be an attacker calling you as a representative of your bank and requesting bank account details from you.
For data security, ensure that you’re clearing your data from your web browser on a regular basis. Consider using a password manager to secure your different passwords and add yet another layer of security. Lastly, remember not to store sensitive data on removable media like flash drives or SD cards, in case those become lost.
Conclusion
Using these above tips will help you remain secure against not only Spectre and Meltdown, but other vulnerabilities that may arise in the future. Remember that security is a layered approach, so the more you can do to protect yourself and your devices, the better.











Discussion